Configuring NetApp hardware-based
encryption
NetApp hardware-based encryption
supports full-disk encryption (FDE) of data as it is written. The data cannot
be read without an encryption key stored on the firmware. The encryption key,
in turn, is accessible only to an authenticated node.
Understanding
NetApp hardware-based encryption
A node authenticates itself to a self-encrypting drive using
an authentication key retrieved from an external key management server or
Onboard Key Manager:
- The external key management server is a third-party
system in your storage environment that serves keys to nodes using the Key
Management Interoperability Protocol (KMIP). It is a best practice to
configure external key management servers on a different storage system
from your data.
- The Onboard Key Manager is a built-in tool that serves
authentication keys to nodes from the same storage system as your data.
You can use NetApp Volume Encryption with hardware-based
encryption to “double encrypt” data on self-encrypting drives.
NetApp Storage Encryption (NSE)
provides full-disk encryption without compromising storage efficiency or
performance
NetApp® Storage Encryption (NSE) is
NetApp’s implementation of full-disk encryption (FDE) using self-encrypting
drives from leading vendors.
NSE is a nondisruptive encryption
implementation that provides comprehensive, cost-effective, hardware-based
security that is simple to use. This single-source solution can increase
overall compliance with industry and government regulations without
compromising storage efficiency.
NSE:
- Supports
the entire suite of storage efficiency technologies from NetApp, including
deduplication, compression, and array-based AV scanning
- Supports
the Gemalto SafeNet KeySecure encryption-key appliance, strengthening and
simplifying long-term key management.
- Helps
you comply with FISMA, HIPAA, PCI, Basel II, SB 1386, and E.U. Data
Protection Directive 95/46/EC regulations using FIPS 140-2 validated
hardware
- Complies
with the OASIS KMIP standard, offering compatibility with other key
managers and encryption devices
Configuring
NetApp Volume Encryption
NetApp Volume Encryption (NVE)
is a software-based technology for encrypting data at rest one volume at a
time. An encryption key accessible only to the storage system ensures that
volume data cannot be read if the underlying device is repurposed, returned,
misplaced, or stolen.
Understanding
NVE
Both data, including Snapshot copies, and metadata are
encrypted. Access to the data is given by a unique XTS-AES-256 key, one per
volume. An external key management server or Onboard Key Manager serves keys to
nodes:
- The external key management server is a third-party
system in your storage environment that serves keys to nodes using the Key
Management Interoperability Protocol (KMIP). It is a best practice to
configure external key management servers on a different storage system
from your data.
- The Onboard Key Manager is a built-in tool that serves
keys to nodes from the same storage system as your data.
Starting with ONTAP 9.7, aggregate and volume encryption is
enabled by default if you have a volume encryption (VE) licence and use an
onboard or external key manager. Whenever an external or onboard key manager is
configured there is a change in how data at rest encryption is configured for
brand new aggregates and brand new volumes. Brand new aggregates will have NetApp
Aggregate Encryption (NAE) enabled by default. Brand new volumes that are not
part of an NAE aggregate will have NetApp Volume Encryption (NVE) enabled by
default.
NetApp Aggregate-level encryption (NAE)
Ordinarily, every encrypted volume is
assigned a unique key. When the volume is deleted, the key is deleted with it.
Starting with ONTAP 9.6, you can use NetApp Aggregate Encryption (NAE) to
assign keys to the containing aggregate for the volumes to be encrypted. When
an encrypted volume is deleted, the keys for the aggregate are preserved. The
keys are deleted only after the last encrypted volume in the aggregate is
deleted.
You must use aggregate-level encryption if
you plan to perform inline or background aggregate-level deduplication.
Aggregate-level deduplication is otherwise not supported by NVE.
Starting with ONTAP 9.7, aggregate and
volume encryption is enabled by default if you have a volume encryption (VE)
licence and use an onboard or external key manager.
NVE and NAE volumes can coexist on the same
aggregate. Volumes encrypted under aggregate-level encryption are NAE volumes
by default. You can override the default when you encrypt the volume.
You can use the volume move command
to convert an NVE volume to an NAE volume, and vice versa. You can replicate an
NAE volume to an NVE volume.
Configuring onboard key management
You
can use the Onboard Key Manager to authenticate cluster nodes to a FIPS drive
or SED. The Onboard Key Manager is a built-in tool that serves authentication
keys to nodes from the same storage system as your data. The Onboard Key
Manager is FIPS-140-2 level 1 compliant.
Initially there is no key managers installed.
Create key manager either On-Board or External.
Provide the pass phrase and create a onboard key manager.
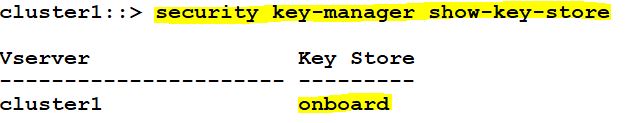
Check the key store and backup key information.
Both the nodes using the Onboard key manager for NetApp Storage Encryption.
Now create a volume with option -encrypt true.
Check the encryption status of that volume using the following command.
Create an aggregate with option encrypt-with-aggr-key true, to create NetApp Aggregate Encryption(NAE).
Check the NAE status.
You can disable the aggregate level encryption by using the following command.
Now move the volume to this non-encrypt aggregate with option encrypt-destination false.
The you can use it vice-versa for enabling the volume encryption with true option.
Now the volume is disabled for encryption.















No comments:
Post a Comment